After finding the SEPT product you want to
purchase, click on BUY and the system will transfer
you to the NORMADOC store which provides the fulfillment process for SEPT.
Every checklist is available in PDF or word format. The latter format allows you to adapt the checklist to your business case and/or a media of your choice such as a web-based excel worksheet. This enables you to demonstrate compliance with the standard in a manner that is most efficient for you.
Every checklist comes with four hours of free consultation. SEPT will answer any question concerning the standard or checklist for 60 days after purchase.
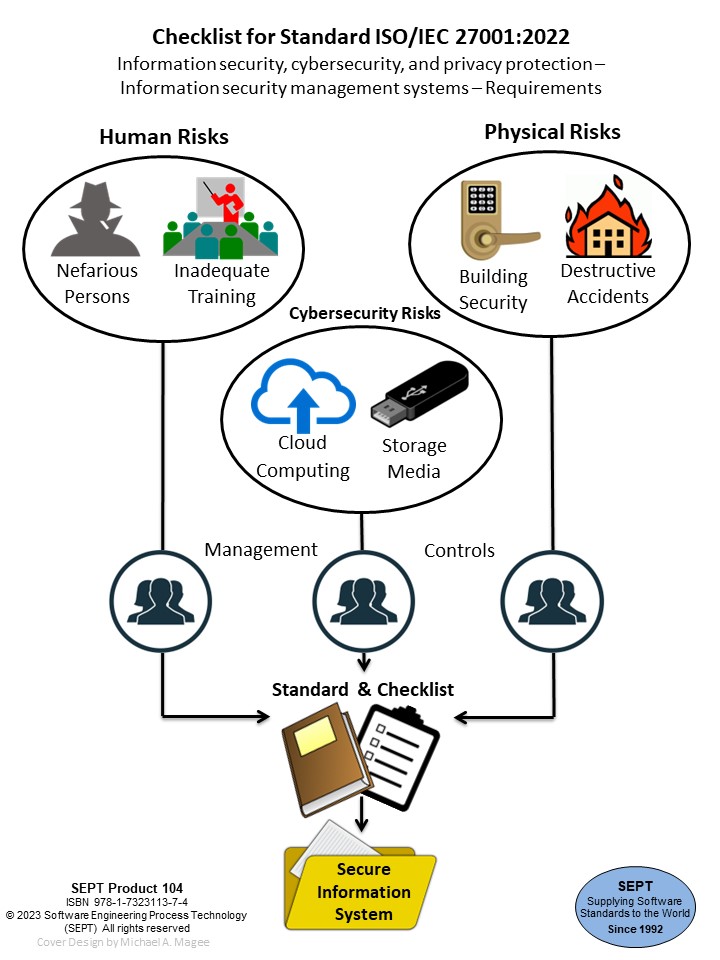
Checklist for Standard ISO/IEC 27001:2022 - Information Security Requirements -
Authors: Andy Coster and Stan Magee Pages: 124
This Software Engineering Process Technology (SEPT) checklist enables an organization to have the confidence that it has created all of the 371 artifacts required by the ISO/IEC 27001:2022 standard as well as additional ones recommended by the experts at SEPT. Each artifact on this checklist is identified as a: policy, procedure, plan, record, document, audit, or review. Listed in tabular form, the checklist provides a clear, concise view of what is required by the standard.
When an artifact has been checked off on the checklist, it means that the physical item exists or that, for a review or audit, evidence exists that the review or audit has been conducted. The checklist thus helps you ensure that you have not only met the standard, but can also demonstrate that fact to any outside organization.For 20+ years SEPT has produced checklists for organizations that require the highest level of proof that they have created all of the artifacts needed to meet the requirements of a particular standard like ISO/IEC 27001:2022 (which has 371 identified artifacts). Our senior staff has many years of experience in developing world class software engineering process standards and checklists. On average, we spend over 500 manhours to construct a checklist for a standard - verifying that it is accurate and no nuance of the standard has been overlooked. Every step along the way in the creation of a checklist is verified by multiple individuals to ensure accuracy.
Creation of artifacts called out in this checklist, if properly constructed, should satisfy any review body that your organization has satisfied the requirements of ISO/IEC 27001:2022.
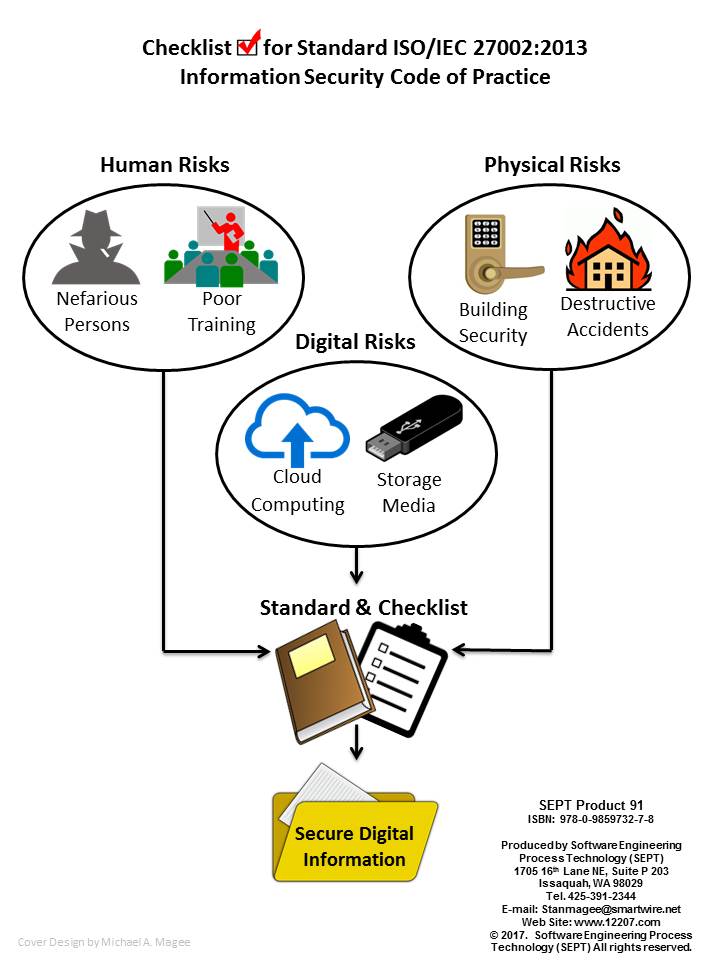
Checklist for Standard ISO/IEC 27002: - Information Security Code of Practice
Author: Andy Coster and Stan Magee Pages: 616
ISO/IEC 27002:2013 gives guidelines for organizational information security standards and information security management practices including the selection, implementation and management of controls taking into consideration the organization's information security risk environment(s).
It is designed to be used by organizations that intend to develop their own information security management practices and controls that meet the Information Security Management System (ISMS) requirements set forth in ISO/IEC 27001.
The updates included in the ISO/IEC 27002:2013 guidelines standard are listed at a high level in an Annexed reference in ISO 27001:2013 as appropriate guidance to demonstrate conformance to that standard. If an organization is interested in testing their conformance to ISO/IEC 27001:2013 this checklist will provide an analysis of the detail in the ISO/IEC 27002 guidelines that forms a part of ISO/IEC 27001:2013.
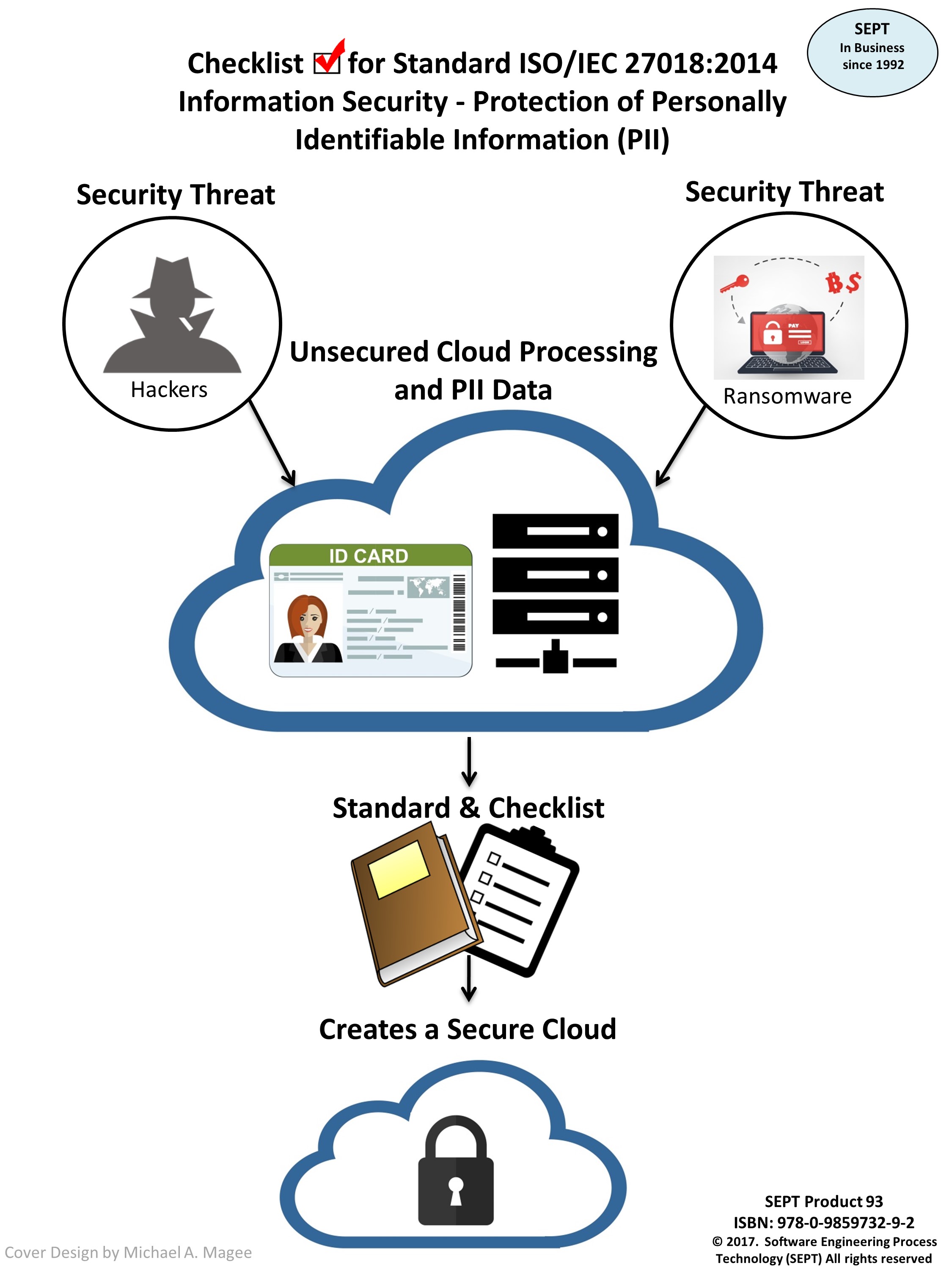
Checklist for Standard ISO/IEC 27018:2014 - Information Security, Protection of Personally Identifiable Information (PII)
Authors: Andy Coster and Stan Magee Pages: 101
Overview ISO/IEC 27018:2014
ISO/IEC 27018 establishes commonly accepted control objectives, controls and guidelines for implementing measures to protect Personally Identifiable Information (PII) in accordance with the privacy principles in ISO/IEC 29100 for the public cloud computing environment.
ISO/IEC 27018 specifies guidelines based on ISO/IEC 27002, taking into consideration the regulatory requirements for the protection of PII which might be applicable within the context of the information security risk environment(s) of a provider of public cloud services.
ISO/IEC 27018 is applicable to all types and sizes of organizations, including public and private companies, government entities, and not-for-profit organizations, which provide information processing services as PII processors via cloud computing under contract to other organizations.
The guidelines in ISO/IEC 27018 might also be relevant to organizations acting as PII controllers; however, PII controllers can be subject to additional PII protection legislation, regulations and obligations, not applying to PII processors. ISO/IEC 27018 is not intended to cover such additional obligations
Annex A to ISO/IEC 27018:2014 specifies new controls and associated implementation guidance which, in combination with the augmented controls and guidance in ISO/IEC 27002, make up an extended control set to meet the requirements for PII protection which apply to public cloud service providers acting as PII processors. These additional controls are classified according to the 11 privacy principles of ISO/IEC 29100.
Purpose of the Standard
More companies are going to the Cloud each day. The “cloud” offers organizations a variety of benefits: cost savings, flexibility and mobile access to information. However, it also raises concerns about data protection and privacy; particularly around personally identifiable information (PII). PII includes any piece of information that can identify a specific user. The more obvious examples include names and contact details or your mother’s maiden name. The cloud processor also has high risk. Security must be extremely high especially if you have a subcontractor doing part of the work. If this data is compromised it could cost a company, customers, money and reputation.
Purpose of the SEPT 27018:2014 Checklist
The task of getting information security under control is daunting. The last thing an organization wants in its security management operation is to call in a Notified Body for certification and to find out that the organization is lacking the correct records or documents for the auditor to examine. If you do not read the standard correctly it could cause a security problem or could increase the cost to become certified. That is why we believe a checklist is important.
For 20 + years Software Engineering Process Technology (SEPT) has been producing checklists for standards that address software issues. To reduce the fog surrounding these types of standards SEPT has been producing checklists for standards since 1994. This is another checklist related to standards for the IT industry that will aid an organization’s compliance with an international information security code of practice.